Lesson 3 - Initial Configuration of Cisco Switch and Router
Lesson 3 - Initial Configuration of Cisco Switch and Router
Understanding technologies requires a skill. Even though not mine, but the best definition of what a skill is, could be summarized in five words: knowledge and one thousand repetitions.
In this lesson, there is no real technology to explain. Instead, you will get familiar with some useful commands we use very often while configuring our routers and switches. This practical exercise however, is going to help hone your skills obtained in the previous lesson.
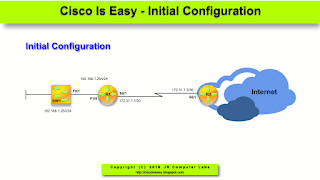
Take a look at our simple topology first:
Switch/router/computer icons designed by: Andrzej Szoblik - http://www.newo.pl
And here's our plan for the initial configuration.
Most of the steps are identical on a switch and a router. That is why I'm presenting, router's configuration only. You have to repeat them on the switch yourself. If the configuration of the switch is different, it is presented as well (step 9 and step 10).
If your prompt shows the user mode '>' you must enter the privileged mode first by typing 'enable':
Then, in order to set the host name on the router you must enter the 'config mode' (you can abreviate the command to 'conf t'):
Finally, you type in:
NOTICE!
The commands take effect immediately as long as their syntax is correct.
2. When you mistype the command in the 'enabled mode' the IOS is trying to resolve this name to ip address. Disable that name resolution.
R1(config)#no ip domain-lookup
3. Protect the 'privileged exec mode' with clear text password. Use 'cisco_enable' as your password.
4. Encrypt the password with 'over-shoulder' algorithm.
R1(config)#service password-encryption
5. Protect the access to the console port 0. Use 'cisco_console' as your password.
In order to do that you have to change the context from 'config mode' to 'line console 0' mode. Pay attention to the prompt! The 'login' keyword is going to prompt the user for the password.
NOTICE!
the 'no login' command would allow the user to access the console 0 WITHOUT asking for the password even if one was configured.
6. Configure the console port 0, so it disconnects you after 5 min. 30 sec. of idleness.
We're still in console 0 prompt so, we can continue configuring console 0.
R1(config-line)#exec-timeout 5 30
R1(config-line)#
If you wanted the console line 0 to never disconnect you during the time of idleness, you would use:exec-timeout 0 0.
7. Configure the console port 0 such, that system messages sent to the screen, do not interfere with what you are typing.
By default, all system messages are sent to the console 0 and they may interfere with what you are currently typing on the console 0 line. If you are accessing the device via telnet/ssh (remotely), you do not see any messages. If you want to see them on the vty lines (remote connection via telnet/ssh), you must type in: 'terminal monitor' in the 'enabled mode'. Here is the command to satisfy the step 7 in our design:
8. After careful consideration you decide to use the most secure access to the 'privileged exec mode'. Disable the previous method and configure the same password using MD5 algorithm to encrypt the password.
As we are still in the line console 0 context (look at the prompt), we need to step back to the 'config mode', and then remove the previous 'enable' password. Next we will proceed with md5 password configuration. If you did not remove the previous 'enable password', system is going to use the more secure one anyway.
R1(config-line)#exit
R1(config)#no enable password
R1(config)#enable secret cisco_enable
9. On the switch assign ip address (use: 192.168.1.253/24) on the management interface Vlan 1.
I assume that you have completed the steps 1-8 on BOTH router and switch. The commands and prompts will be identical. Now, you can assign ip address on Vlan 1 interface.
10. Configure the switch to use the default-gateway (address of the default gateway: 192.168.1.254/24) in case it is managed remotely from another subnet or network.
We need to step back to 'config mode' from interface Vlan1 mode to accomplish the task.
11. Enable the router's interface FastEthernet1/0. Use 192.168.1.254/24 address.
12. Enable the interface facing the Internet Serial0/1 (we pretend it is the public interface). Use ip address 172.31.1.1/30.
Even though we are currently in F1/0 interface context (look at the prompt), we can jump directly towards s0/1 without typing 'exit' first. If you use real routers (not dynamips), one end of the connection must use DCE cable and the other DTE cable. They are connected back-to-back and DCE interface must be set up with the clock rate.
13. Enable the remote access to your devices via telnet. Use password 'cisco_remote'.
Remote access connections are service by special, virtual lines called vty. Here, we will use vty lines 0 through 4, allowing only five concurrent connections via telnet.
R1(config-if)#login
14. After careful consideration you decide to use ssh as the remote access method rather than telnet. Configure that.
This is going to be the most complex part in our lab. Below are four steps need to complete the task.
a) Configure system domain-name. Without the domain name, IOS cannot generate rsa keys used for encryption and decryption (public/private). The domain name can be any name you choose to use (here: ccna.local) but company's real name is a good idea.
R1(config-line)#exit
b) When you type the below command the system will ask you what should be the length of the keys. Choose 1024 value. IOS will take a few seconds to generate them and automatically start SSH server. Wait till it's done.
c) Create a user account that will be used for ssh access (here: user=admin, password=S3cr3t).
R1(config)#username admin password cisco_remote
d) Enable ssh protcol and disable telnet on vty lines 0 4. Make sure that ssh will use locally created user (admin) for ssh connections. This is done using 'login local' command.
15. Save the configuration on both switch and the router so it is available after reload/power cycle.
R1#copy running-config startup-config
In this lesson, there is no real technology to explain. Instead, you will get familiar with some useful commands we use very often while configuring our routers and switches. This practical exercise however, is going to help hone your skills obtained in the previous lesson.
Take a look at our simple topology first:
Switch/router/computer icons designed by: Andrzej Szoblik - http://www.newo.pl
And here's our plan for the initial configuration.
- Configure the host names on both the switch and the router (SW1 and R1 respectively).
- When you mistype the command in the 'enabled mode' the IOS is trying to resolve this name to ip address. Disable that name resolution.
- Protect the 'privileged exec mode' with clear text password. Use 'cisco_enable' as your password.
- Encrypt the password with 'over-shoulder' algorithm.
- Protect the access to the console port 0. Use 'cisco_console' as your password.
- Configure the console port 0, so it disconnects you after 5 min. 30 sec. of idleness.
- Configure the console port 0 such, that system messages sent to the screen, do not interfere with what you are typing.
- After careful consideration you decide to use the most secure access to the 'privileged exec mode'. Disable the previous method and configure the same password using MD5 algorithm to encrypt the password.
- On the switch assign ip address (use: 192.168.1.253/24) on the management interface Vlan 1.
- Configure the switch to use the default-gateway (address of the default gateway: 192.168.1.254/24) in case it is managed remotely from another subnet or network.
- Enable the router's interface FastEthernet1/0. Use 192.168.1.254/24 address.
- Enable the interface facing the Internet Serial0/1 (we pretend it is the public interface). Use ip address 172.31.1.1/30.
- Enable the remote access to your devices via telnet. Use password 'cisco_remote'.
- After careful consideration you decide to use ssh as the remote access method rather than telnet. Configure that.
- Save the configuration on both switch and the router so it is available after reload/power cycle.
Solution:
1. Configure the host names on both the switch and the router (SW1 and R1 respectively). Most of the steps are identical on a switch and a router. That is why I'm presenting, router's configuration only. You have to repeat them on the switch yourself. If the configuration of the switch is different, it is presented as well (step 9 and step 10).
If your prompt shows the user mode '>' you must enter the privileged mode first by typing 'enable':
Router>enable
Router#
Then, in order to set the host name on the router you must enter the 'config mode' (you can abreviate the command to 'conf t'):
Router#configure terminal
Router(config)#
Finally, you type in:
Router(config)#hostname R1
R1(config)#NOTICE!
The commands take effect immediately as long as their syntax is correct.
2. When you mistype the command in the 'enabled mode' the IOS is trying to resolve this name to ip address. Disable that name resolution.
R1(config)#no ip domain-lookup
3. Protect the 'privileged exec mode' with clear text password. Use 'cisco_enable' as your password.
R1(config)#enable password cisco_enable
4. Encrypt the password with 'over-shoulder' algorithm.
R1(config)#service password-encryption
5. Protect the access to the console port 0. Use 'cisco_console' as your password.
In order to do that you have to change the context from 'config mode' to 'line console 0' mode. Pay attention to the prompt! The 'login' keyword is going to prompt the user for the password.
NOTICE!
the 'no login' command would allow the user to access the console 0 WITHOUT asking for the password even if one was configured.
R1(config)#line console 0
R1(config-line)#password cisco_console
R1(config-line)#login
6. Configure the console port 0, so it disconnects you after 5 min. 30 sec. of idleness.
We're still in console 0 prompt so, we can continue configuring console 0.
R1(config-line)#exec-timeout 5 30
R1(config-line)#
If you wanted the console line 0 to never disconnect you during the time of idleness, you would use:exec-timeout 0 0.
7. Configure the console port 0 such, that system messages sent to the screen, do not interfere with what you are typing.
By default, all system messages are sent to the console 0 and they may interfere with what you are currently typing on the console 0 line. If you are accessing the device via telnet/ssh (remotely), you do not see any messages. If you want to see them on the vty lines (remote connection via telnet/ssh), you must type in: 'terminal monitor' in the 'enabled mode'. Here is the command to satisfy the step 7 in our design:
R1(config-line)#logging synchronous
8. After careful consideration you decide to use the most secure access to the 'privileged exec mode'. Disable the previous method and configure the same password using MD5 algorithm to encrypt the password.
As we are still in the line console 0 context (look at the prompt), we need to step back to the 'config mode', and then remove the previous 'enable' password. Next we will proceed with md5 password configuration. If you did not remove the previous 'enable password', system is going to use the more secure one anyway.
R1(config)#enable secret cisco_enable
9. On the switch assign ip address (use: 192.168.1.253/24) on the management interface Vlan 1.
I assume that you have completed the steps 1-8 on BOTH router and switch. The commands and prompts will be identical. Now, you can assign ip address on Vlan 1 interface.
SW1>enable
SW1#conf t
SW1(config)#interface vlan 1
SW1(config-if)#ip address 192.168.1.253 255.255.255.0
SW1(config-if)#no shutdown10. Configure the switch to use the default-gateway (address of the default gateway: 192.168.1.254/24) in case it is managed remotely from another subnet or network.
We need to step back to 'config mode' from interface Vlan1 mode to accomplish the task.
SW1(config-if)#exit
SW1(config)#ip default-gateway 192.168.1.254
11. Enable the router's interface FastEthernet1/0. Use 192.168.1.254/24 address.
R1(config)#interface f1/0
R1(config-if)#ip address 192.168.1.254 255.255.255.0
R1(config-if)#no shutdown
12. Enable the interface facing the Internet Serial0/1 (we pretend it is the public interface). Use ip address 172.31.1.1/30.
Even though we are currently in F1/0 interface context (look at the prompt), we can jump directly towards s0/1 without typing 'exit' first. If you use real routers (not dynamips), one end of the connection must use DCE cable and the other DTE cable. They are connected back-to-back and DCE interface must be set up with the clock rate.
R1(config-if)#interface s0/1
R1(config-if)#ip address 172.31.1.1 255.255.255.252
R1(config-if)#no shutdown
13. Enable the remote access to your devices via telnet. Use password 'cisco_remote'.
Remote access connections are service by special, virtual lines called vty. Here, we will use vty lines 0 through 4, allowing only five concurrent connections via telnet.
R1(config-if)#line vty 0 4
R1(config-if)#password cisco_remoteR1(config-if)#login
14. After careful consideration you decide to use ssh as the remote access method rather than telnet. Configure that.
This is going to be the most complex part in our lab. Below are four steps need to complete the task.
a) Configure system domain-name. Without the domain name, IOS cannot generate rsa keys used for encryption and decryption (public/private). The domain name can be any name you choose to use (here: ccna.local) but company's real name is a good idea.
R1(config-line)#exit
R1(config)#ip domain-name ccna.local
R1(config)#b) When you type the below command the system will ask you what should be the length of the keys. Choose 1024 value. IOS will take a few seconds to generate them and automatically start SSH server. Wait till it's done.
R1(config)#crypto key generate rsa
R1(config)#
c) Create a user account that will be used for ssh access (here: user=admin, password=S3cr3t).
R1(config)#username admin password cisco_remote
R1(config)#
d) Enable ssh protcol and disable telnet on vty lines 0 4. Make sure that ssh will use locally created user (admin) for ssh connections. This is done using 'login local' command.
R1(config)#line vty 0 4
R1(config-line)#transport input ssh
R1(config-line)#login local
R1(config-line)#end
R1#
15. Save the configuration on both switch and the router so it is available after reload/power cycle.
R1#copy running-config startup-config
Comments