QinQ with Cisco Catalyst switches
QinQ with Cisco Catalyst switches
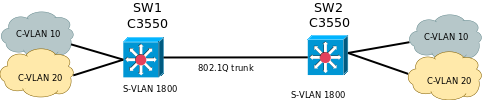
Below a simple topology using QinQ tagging (officially known as IEEE 802.1ad or unofficially IEEE 802.1 QinQ )
on Cisco Catalyst C3550 switches.
C-VLANS 10 and 20 come from customer side and are encapsulated in the S-VLAN 1800.
This feature is also called VLAN double tagging or Vlan stacking, or Nested VLANs (Allied Telesis) or vMAN
This feature is also called VLAN double tagging or Vlan stacking, or Nested VLANs (Allied Telesis) or vMAN
technology ( Extreme Networks).
To simulate the two end clients, I use two Linux computers that allows easy creation of VLANs on ethernet ports.
Network configuration on Linux computers
LINUX PC1
$ sudo vconfig add eth5 1800
Added VLAN with VID == 1800 to IF -:eth5:-
$ sudo vconfig add eth5.1800 10
Added VLAN with VID == 10 to IF -:eth5.1800:-
$ sudo vconfig add eth5.1800 20
Added VLAN with VID == 20 to IF -:eth5.1800:-
$ sudo ip addr add 10.10.10.1/24 dev eth5.1800.10
$ sudo ip addr add 20.20.20.1/24 dev eth5.1800.20
$ ip addr
14: eth5.1800@eth5: <broadcast> mtu 1500 qdisc noqueue state UP
link/ether 00:e0:4c:36:00:0a brd ff:ff:ff:ff:ff:ff
inet6 fe80::2e0:4cff:fe36:a/64 scope link
valid_lft forever preferred_lft forever
15: eth5.1800.10@eth5.1800: <broadcast> mtu 1500 qdisc noqueue state UP
link/ether 00:e0:4c:36:00:0a brd ff:ff:ff:ff:ff:ff
inet 10.10.10.1/24 scope global eth5.1800.10
valid_lft forever preferred_lft forever
inet6 fe80::2e0:4cff:fe36:a/64 scope link
valid_lft forever preferred_lft forever
16: eth5.1800.20@eth5.1800: <broadcast> mtu 1500 qdisc noqueue state UP
link/ether 00:e0:4c:36:00:0a brd ff:ff:ff:ff:ff:ff
inet 20.20.20.1/24 scope global eth5.1800.20
valid_lft forever preferred_lft forever
inet6 fe80::2e0:4cff:fe36:a/64 scope link
valid_lft forever preferred_lft forever
LINUX PC2
$ sudo vconfig add eth4 1800
Added VLAN with VID == 1800 to IF -:eth4:-
$ sudo vconfig add eth4.1800 10
Added VLAN with VID == 10 to IF -:eth4.1800:-
$ sudo vconfig add eth4.1800 20
Added VLAN with VID == 20 to IF -:eth4.1800:-
$ sudo ip addr add 10.10.10.2/24 dev eth4.1800.10
$ sudo ip addr add 20.20.20.2/24 dev eth4.1800.20
$ ip addr 8: eth4.1800@eth4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP
link/ether 00:10:a3:09:e6:bb brd ff:ff:ff:ff:ff:ff
inet6 fe80::210:a3ff:fe09:e6bb/64 scope link
valid_lft forever preferred_lft forever
9: eth4.1800.10@eth4.1800: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP
link/ether 00:10:a3:09:e6:bb brd ff:ff:ff:ff:ff:ff
inet 10.10.10.2/30 scope global eth4.1800.10
inet6 fe80::210:a3ff:fe09:e6bb/64 scope link
valid_lft forever preferred_lft forever
10: eth4.1800.20@eth4.1800: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP
link/ether 00:10:a3:09:e6:bb brd ff:ff:ff:ff:ff:ff
inet 20.20.20.2/30 scope global eth4.1800.20
inet6 fe80::210:a3ff:fe09:e6bb/64 scope link
valid_lft forever preferred_lft forever
Cisco Catalyst switches configuration
SW1
#show system mtu
System MTU size is 1546 bytes
interface FastEthernet0/2
description --dot1q-tunnel_SW1--
switchport access vlan 1800
switchport mode dot1q-tunnel
no ip address
l2protocol-tunnel cdp
l2protocol-tunnel stp
l2protocol-tunnel vtp
no cdp enable
spanning-tree bpdufilter enable
end
interface FastEthernet0/19
description --To SW2 Fa0/19--
switchport trunk encapsulation dot1q
switchport mode trunk
end
SW2
#show system mtu
System MTU size is 1546 bytes
interface FastEthernet0/2
description --dot1q-tunnel_SW2--
switchport access vlan 1800
switchport mode dot1q-tunnel
no ip address
l2protocol-tunnel cdp
l2protocol-tunnel stp
l2protocol-tunnel vtp
no cdp enable
spanning-tree bpdufilter enable
end
interface FastEthernet0/19
description --To SW1 Fa0/19--
switchport trunk encapsulation dot1q
switchport mode trunk
end
Verifying
a) From Linux computer
On the linux computers I'm using tcpdump to capture the packets on interface eth5 ( Linux PC 1) . In the packets we see that it contains the S-VLAN 1800 and C-VLANs 10 and 20.
$ sudo tcpdump -i eth5 -ne vlan -c 10
23:10:43.282757 00:10:a3:09:e6:bb > 00:e0:4c:36:00:0a, ethertype 802.1Q (0x8100), length 1450: vlan 1800, p 0, ethertype 802.1Q, vlan 20, p 0, ethertype IPv4, 20.20.20.2 > 20.20.20.1: ICMP echo request, id 8509, seq 524, length 1408
23:10:43.284015 00:e0:4c:36:00:0a > 00:10:a3:09:e6:bb, ethertype 802.1Q (0x8100), length 1450: vlan 1800, p 0, ethertype 802.1Q, vlan 20, p 0, ethertype IPv4, 20.20.20.1 > 20.20.20.2: ICMP echo reply, id 8509, seq 524, length 1408
23:10:43.323901 00:e0:4c:36:00:0a > 00:10:a3:09:e6:bb, ethertype 802.1Q (0x8100), length 1350: vlan 1800, p 0, ethertype 802.1Q, vlan 10, p 0, ethertype IPv4, 10.10.10.1 > 10.10.10.2: ICMP echo request, id 5068, seq 196, length 1308
23:10:43.324633 00:10:a3:09:e6:bb > 00:e0:4c:36:00:0a, ethertype 802.1Q (0x8100), length 1350: vlan 1800, p 0, ethertype 802.1Q, vlan 10, p 0, ethertype IPv4, 10.10.10.2 > 10.10.10.1: ICMP echo reply, id 5068, seq 196, length 1308
b) Configuring the Catalyst Switched Port Analyzer
Using the SPAN feature, we can mirror the traffic from the trunk port F0/19 to interface Fa0/3.
SW2(config)#monitor session 1 source interface Fa0/19
SW2(config)#monitor session 1 destination interface Fa0/3 encapsulation dot1q
SW2#sh monitor session 1
Session 1
---------
Type : Local Session
Source Ports :
Both : Fa0/19
Destination Ports : Fa0/3
Encapsulation : DOT1Q
Ingress : Disabled
Can also use the following :
SW2(config)#monitor session 1 source interface Fa0/19
SW2(config)#monitor session 1 filter vlan 1800
SW2(config)#monitor session 1 destination interface Fa0/3 encapsulation dot1q
SW2#show monitor session 1
Session 1
---------
Type : Local Session
Source Ports :
Both : Fa0/19
Destination Ports : Fa0/3
Encapsulation : DOT1Q
Ingress : Disabled
Filter VLANs : 1800
Using wireshark we capture the mirrored traffic on interface Fa0/3.
Analyzing the packets we see both VLANs ( highlighted blue).


Comments