|
Introduction
- Firstly , we Download Prorat .
- We Create a Bind Server .
- Examples : How to hack Backtrack 5
- Examples : Windows to Windows hacking
Download ProRat
- Before doing Experiment with Backtrack 5 , first you need to install Prorat V1.9 on your windows Xp Machine .
- Download : http://www.prorat.net/downloads.php?id=ProRat_v1.9_Fix2(ZipPass:pro)
- Password of this Zip file is : pro
- After download extract the Prorat and Run it .
Creating Server
- Click on the create button and then on the Create ProRat Server button.
- See the below image for more details -
- Enter the IP in the ProConnective Notification
- If you don’t know the IP address click the red arrow and It will fill IP address automatically.
- Mail Notification :
In this option , you have to enter your email address , so whenever the
server is installed into your victim computer ,it will send a
notification in your mail id .
- See the below image for more details -
GENERAL SETTINGS TAB
- Here you can do some settings .
- See the below image for details -
- In General Settings , you can also configure a fake message .
- See the below image -
BINDING FILE
- Click on ' Bind with file ' on the sidebar.
- You can bind it with a text document or Image File.
- See the below image for more details -
SERVER EXTENSION
- From here you can Select the Server Extension.
- Se the below image for the extensions -
SERVER ICON
- Now Click on server Icon and choose the icon and click on Create server.
CLICK ON CREATE SERVER
- Now, when all things are done, hit on “Create server” and you will get server created in Prorat directory.
- This server is used for remote pc access.
- Now,
when you have created PRORAT server, next step is to send this server
to victim computer and then use PRORAT for remote pc access.
- Now,
when you have created PRORAT server, next step is to send this server
to victim computer and then use PRORAT for remote pc access.
Connecting To Backtrack 5
- Enter the ip address of victim machine and click on the connect button.
- See the below image for more details -
EXAMPLE 1 : PC INFORMATION
- Here you can see the PC info of Backtrack 5 .
- See the below image for details -
EXAMPLE 2: Flip the Backtrack Screen
- From ProRat , you can also flip the Backtrack 5 Screen .
- See the below image for more details -
EXAMPLE 3: SENDING MESSAGE
- Sending Message to Backtrack 5 .
- See the below image for details -
Victim (Backtrack 5 ) Machine
EXAMPLE 4: SCREENSHOT
- Through Prorat , you can take a screen shot of a Victim( Backtrack 5) PC.
- See the below image for more details -
EXAMPLE 5: CHAT WITH VICTIM (BACKTRACK) MACHINE
- In this example , hacker (hackingDNA) is chatting with Victim ( Backtrack 5 ) Machine.
- See the below image for more details -
Windows to Windows Hacking with ProRat
These all images from here are a year old examples but it help you to understand what you can do with ProRat in Windows .
- Example 1 : Cross Chatting between Victim & Hacker.
Example 2: Run cmd on Remote Machine
- Through ProRat , running command prompt on Remote Machine or Victim Machine .
- See the below image -
Example 3: Open Control Panel on Victim Machine
- See the below image for details -
Example 4 : Flip the Victim Screen
Example 5 : Accessing Victim C Drive via ftp
- See the below image for more details -
Example 6 : Hide the Start buton
- See the below image for more details -
Example 7 : Keylogger
- Hack the victim keystrokes using keylogger.
- See the below image for more details -
Example 8 : Matrix Chat
- Chat Session between hacker and Victim in a Matrix Style .
- See the below image for more details -
Example 9 : Message Sending
- Send any message to Victim PC.
Example 10 : Open Paint On Victim Machine , if he is using Windowx XP
Example 11 : Registry Editor
- Victim Registory Editing Service on Hackers Machine .
- See the below image for more details -
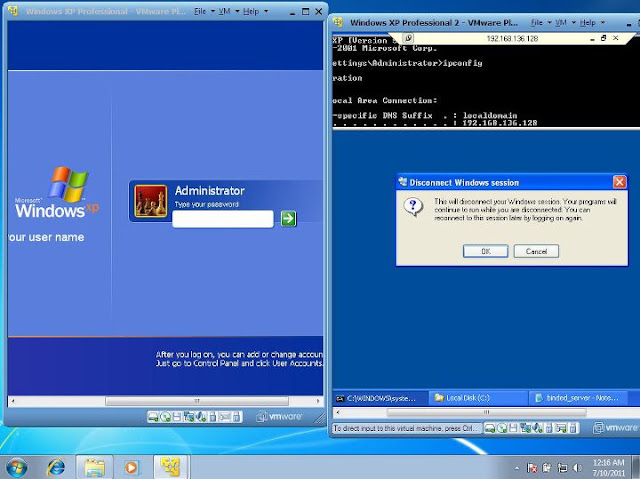
Example 12 : Remote Desktop
- With ProRat, hacker takes Victim Machine on Remote .
- See the below image -
This is how after setting a backdoor on your system , a hacker can easily
- Take your PC on a Remote
- He can grab your Keystrokes through a Keylogger .
- He can take a screenshot of a Victim Screen .
- He can also take a picture from a Victim Web Cam .
- He can access your directories , Registry , command shell , registry editor , control panel etc.
- This all we can done with single IP and setting a Trojan on Victim Machine.
Security Measures
- Its Important you should have a Firewall installed on your system .
- Update AntiVirus Regularly .
- Use
Update Antiviruses , it protect you from these trojan , viruses and
even what we created a Bindserver trojan . It can detect and deleted all
the viruses
- An update antivirus help you to safe from these Trojans and Viruses .
- I am expecting , this tutorial help you a lot to understand lots of things .
- It a good Tool for practising and learning .
- Use this tool for learning purpose only .
The Reason why we can do some Activities or create a backdoor with Backtrack 5 is Wine , which can run exe file on Backtrack .
I hope you like this tutorial , if you want to say something , drop a message here or you can visit our facebook page .
|






























Comments