INTRODUCTION
Snort
is an open source network intrusion prevention and detection system
(IDS/IPS) developed by Sourcefire. Combining the benefits of signature,
protocol, and anomaly-based inspection, Snort is the most widely
deployed IDS/IPS technology worldwide.
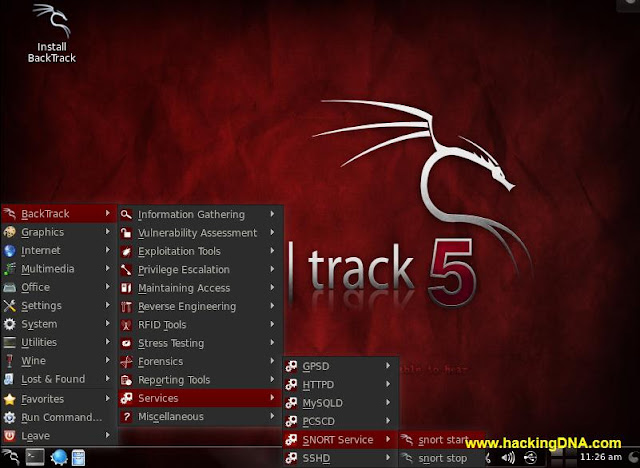
HOW TO OPEN SNORT ON BACKTRACK 5
- Backtrack > Services > Snort Services > snort start
- See the below image for more help -
 |
| HOW TO OPEN SNORT ON BACKTRACK 5 |
SNORT STARTED
- Snort started .
- See the below image for more help -
 |
| SNORT STARTED |
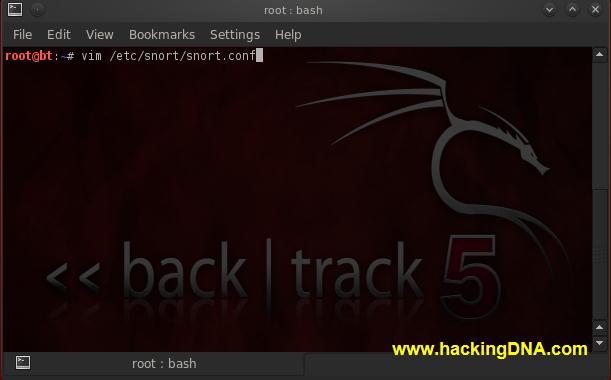
CONFIGURE SNORT
- To configure snort , we use vim editor .
- To open snort configuration file , enter the command as shown in the below image .
- See the below image for command -
 |
| OPENING CONFIG FILE WITH VIM EDITOR |
SNORT CONFIG FILE OPENED
 |
| SNORT CONGURATION |
CONFIG HERE
- This is the area where you have to work .
- Now
the line where i use the yellow box and there you will find a line look
like this var HOME_NET any . Now replace this any to your own internal
ip address .
- In my case my ip address is 192.168.72.129 ( as shown in terminal also ).
- If you don't know your own ip address then use the ifconfig command .
- And at the end save this file by pressing ' Esc key then :wq ' then press enter.
- Note : To enter text in vim press ' i ' .
- See the below image for more help -
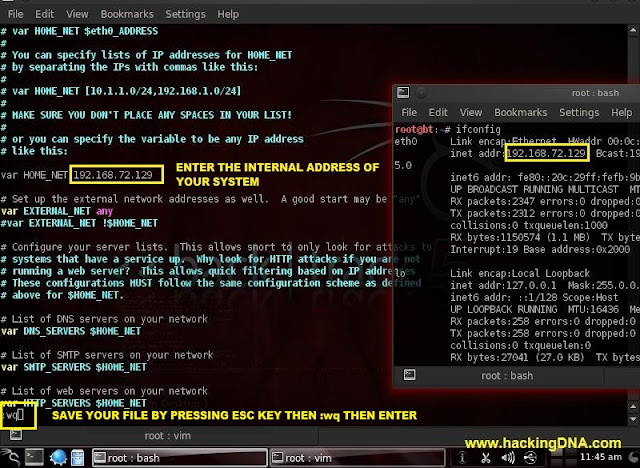 |
| SNORT CONGURATION |
RESTART SNORT
- Now restart snort , by entering the command as shown below.
- See the below image for more details-
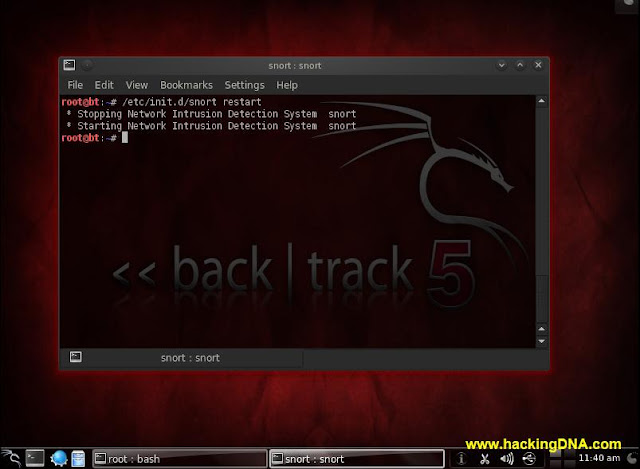 |
| SNORT RESTARTED |
EXAMPLES
Here is use Backtrack 5r3 as a snort machine ( IDS ) and Kali Linux as a attacker machine .
Both are open source linux so easy for you to download .
Now without wasting time see the examples
USING DMITRY FROM KALI LINUX
- Here i perform the Deepmagic Information Gathering Tool also known as 'Dmitry'.
- I used this tool to scan for TCP Ports .
ATTACKER MACHINE
- I look that Kali Linux uses dmitry to performing tcp scan on snort machine ( 192.168.72.129).
- See the below image for more details -
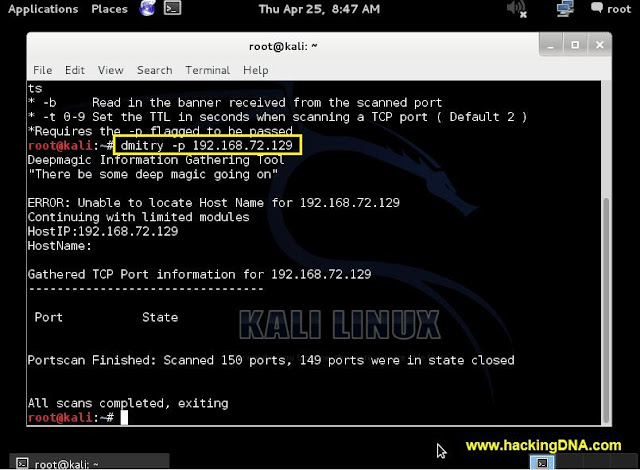 |
| SNORT DETECTION EXAMPLE 1 |
IDS SNORT CAUGHT SOMETHING
- Here you can see that Snort has caught something .
- It shows a Tcp port scan is performed by the 192.168.72.128 ip address.
- Its a very useful information.
- See the below image for more details -
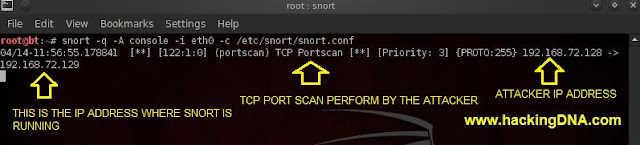 |
| SNORT DETECTION EXAMPLE 1 |
EXAMPLE 2 : PERFORM OS DETECTION SCAN
- Here i used nmap to perform " OS DETECTION SCAN ".
- Command i used : nmap -v -A 192.168.72.129
- See the below image of performing OS Detection scan on kali linux .
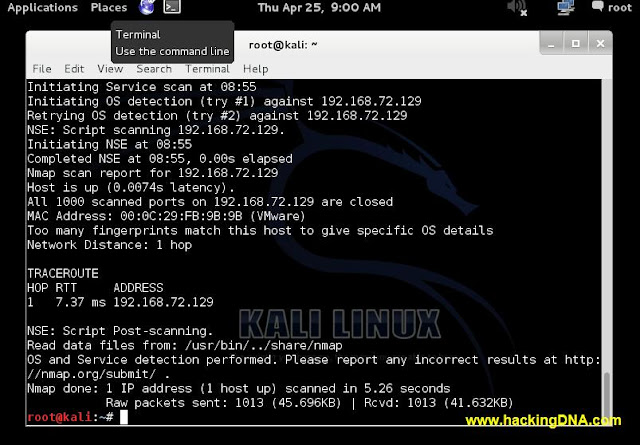 |
| SNORT DETECTION EXAMPLE 2 |
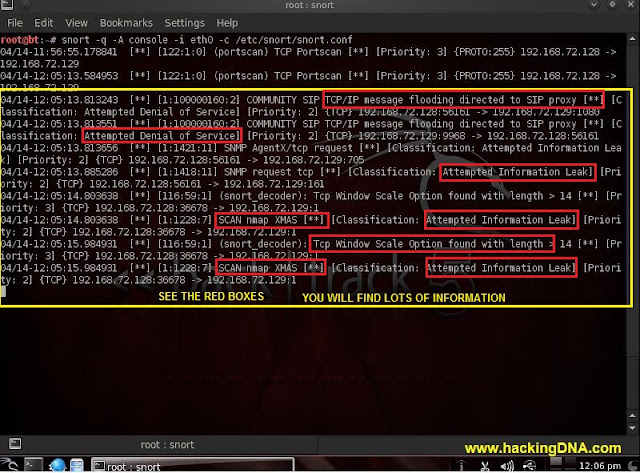
SNORT DETECTION
- Now the best thing , you can see the behaviour of the scan that is performed by nmap .
- See the red boxes that i have put , it shows so many things.
- See the below image for more help-
 |
| SNORT DETECTION EXAMPLE 2 |
CONCLUSION
- So this is how you can use snort on backtrack 5.
- Good in aspect of security .
- You can use it to understand the behaviour of the attack .
- There are lots of things you can do , use your ninja skills and sharp your security .
- Thats it . Thank you for reading .
| 










Comments