- I
don't want any newcomer start learning ethical hacking , penetration
testing by exploiting the real targets ( eg corporate network , or
college network ) . I want you to play safe .
- With
this kept in mind today i decided to create our own hacking labs , so
each of you learn real ethical hacking in real ethical manner without
broken any cyber law .
- So our first HACKING LAB is simple , we only use 2 OS i.e KALI LINUX and METASPLOITABLE .
KALI LINUX
- I hope you all know about KALI LINUX , if not then go to KALI website :
- Website link : http://www.kali.org/
- Download your kali linux if you are downloaded yet .
 |
| KALI LINUX |
METASPLOITABLE
 |
| METASPLOITABLE |
SOFTWARE REQUIREMENTS
- Oracle Virtual Box
- Operating System : Kali Linux & Metasploitable
- Laptop or Desktop
After all your requirements fullfilled time to setup a lab .
SETTING UP A LAB
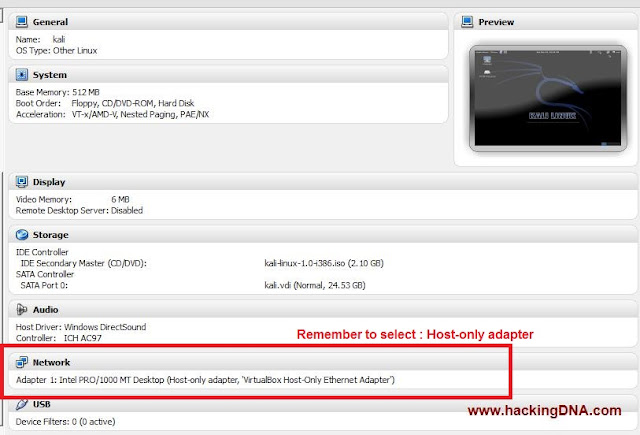
Settings of Kali Linux
- While setting up a hacking lab , remember few things -
- Select Network adapter as : Host only adapter .
- Rest of the installation is normal .
- See the below image for more help -
 |
| KALI LINUX SETTINGS |
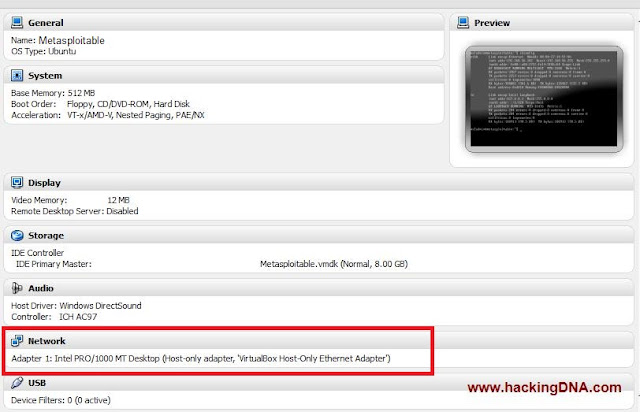
Settings of Metasploitable
- RAM : 512
- Network : Host-only adapter
- See the below image for more details of setting -
 |
| METASPLOITABLE SETTINGS |
Once you are done with settings , start both of your systems .
DESKTOP VIEWS
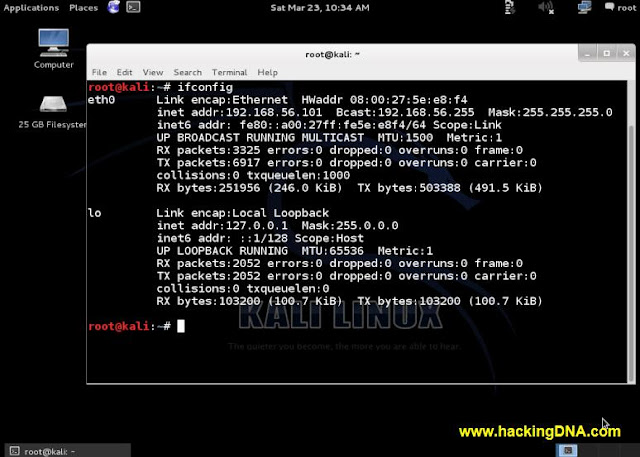
KALI LINUX
- I am loving it , KALI LINUX desktop view with its ip address 192.168.56.101.
- See the below image for more details -
 |
| KALI LINUX DESKTOP VIEW WITH IP ADDRESS |
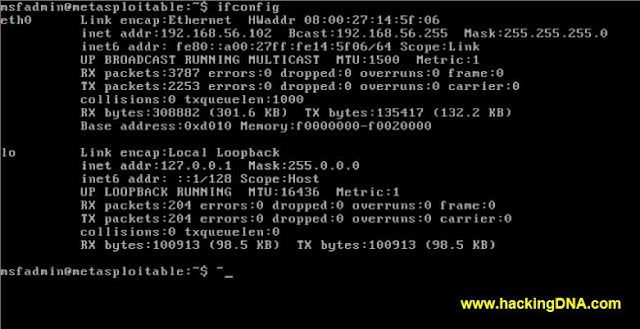
METASPLOITABLE
- Metasploitable ( vulnerable virtual machine )
- Ip Address : 192.168.56.102
- See the below image for more details -
 |
| METASPLOITABLE DESKTOP WITH ITS IP ADDRESS |
So our hacking lab 01 is ready . Now are you ready to test your penetration testing skills .
Lets start with the simple scanning through KALI LINUX .
Nmap
- Perform a tcp connect scan .
- See the below image for the results
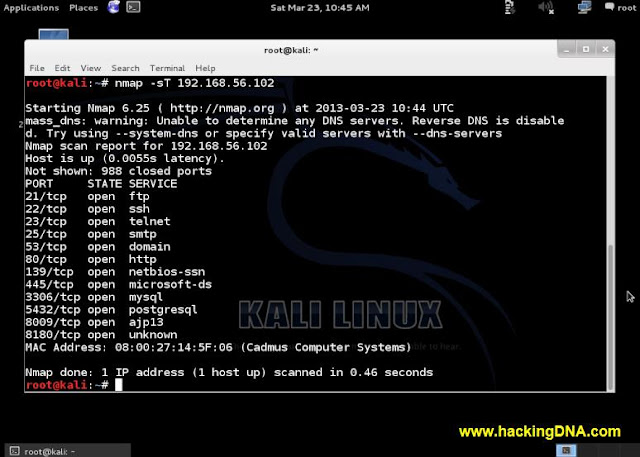 |
| NMAP SCANNING |
- Wow !!! so many ports are open .
- Now explore www.abiadonis.blogspot.com once
again , perform different command , use msfconsole to exploit the
vulnerabilities . Also try to learn how to access metasploitable through
telnet .
- There are so many things you can do . Go through every tutorial of www.abiadonis.blogspot.com and learn from it .
I
LEAVE THIS TUTORIAL HERE ,WANT YOU TO PARTICIPATE IN THIS TUTORIAL AND
POST YOUR EXAMPLE SCREENSHOTS ON FACEBOOK .WAITING FOR YOUR SCREENSHOTS .
- REMEMBER : Self learning , practising help you to understand the subject .
- Post your examples screenshots on facebook Abi DA Adonis page and I upload it in this tutorial with your name .
- Keep following because lots of new tutorials still to come . Keep following us . Happy hacking .








Comments